
Cybersecurity Vs. Human Nature in Healthcare
Recently, I got an email (pictured below) from Adam Gale, KLAS’ fearless leader. But, when I got this email it raised a few red flags for me:
- Contrary to what this email might suggest, Adam doesn’t actually speak like a robot. “I need you to complete a task for me.” Right. Sure thing, Replicant.
- Adam’s office is just down the hall, usually a “quick request” means swinging by my desk. Also, why do you need to text me for a “quick request” if you can already contact me via email? Maybe Adam didn’t want our correspondence to be tracked by IT – which feels a little cloak-and-dagger for a guy who’s built his life on “honest, accurate and impartial” data.
- There’s no signature at the bottom of the email which is a standard practice for the company.
This was obviously a phishing email cleverly spoofing Adam’s account. Several of us in the office received the email and thankfully I don’t think anyone has handed out their cell number, yet. Unfortunately for fake-Adam, his “quick request” will remain unfulfilled.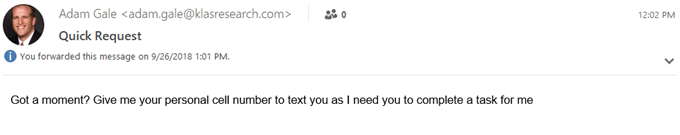
But this did bring to mind a question recently raised during the cybersecurity panel at the 2018 Digital Health Investment Symposium (DHIS). “What are the biggest problems you’re trying to solve in your organization, and how are you leveraging technology to solve them?”
The three DHIS panelists were; Daniel Bowden of Sentara Healthcare, Nassar Nizami of Thomas Jefferson University, and Karl West of Intermountain Healthcare. Each panelist discussed topics that I think resonate in the larger HIT community: moving their organization to the cloud, managing virtual visits across their IDN, and trying make sense of and secure digital landscapes that sometimes involve over 1,500 different applications.
As I listened, I was reminded of this rhetorical question: “Who wins in a fight? A multi-million-dollar, bleeding edge cybersecurity system or one negligent click?”
In some ways, those tasked with cybersecurity in healthcare feel stuck in a lose-lose situation. They can’t afford to ignore the technological risks they face, and so they must spend deeply to create a cohesive cybersecurity plan.
KLAS has seen the overwhelming majority of provider organizations increase their security budgets over the last couple of years. Yet, despite those deep investments of time and resources, all their planning can be undone by a careless employee.
As Karl West from Intermountain put it, “I tell my team all the time: Technology isn’t the answer. People and processes are key to our success.” He argued in favor of better education for employees and caregivers on how to properly, securely, perform their care responsibilities.
Daniel Bowden, VP and CISO at Sentara Healthcare, explained that for most cybersecurity plans, there’s what they called a “continuum of maturity.” And often the employee education piece of a cybersecurity plan falls into place somewhere after those big technological investments.
For Sentara Healthcare, part of this focus on employees means their security team needs to build around an understanding of, “who you are, what you know, what you have and what you do.” Those are the factors they use to determine privacy and security access and reporting.
The benefit? This allows the Sentara team to become increasingly granular in their level of employee risk assessment.
At the end of the day the risk of internal carelessness, more than the risk of technological gaps, keeps CISOs on their toes. If the discussions held during DHIS18 are any indication, cybersecurity vendors that promote and support processes that help mitigate that risk in new, innovative ways stand to be very successful.
Curious about the Digital Health Investment Symposium? Email us!
Photo Cred: Shutterstock, Abscent